SECURING IoT Companion apps
As the Internet of Things (IoT) continues to permeate various aspects of our lives, the security of IoT companion apps becomes increasingly critical. These applications serve as the gateway between users and their IoT devices, facilitating remote control, monitoring, and management. Therefore, ensuring the security of these companion apps is paramount to safeguarding the privacy and integrity of IoT ecosystems.
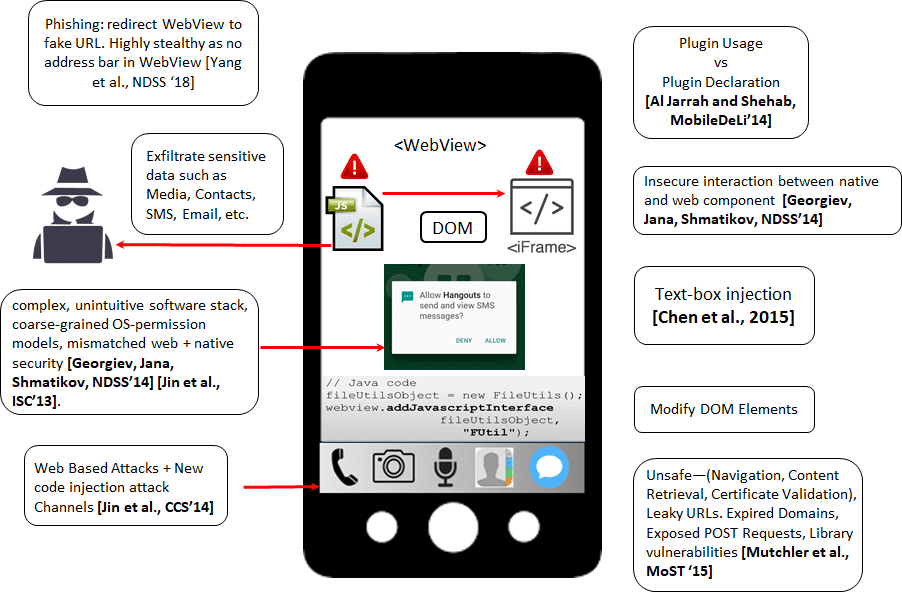
Text box injection, in the context of mobile apps, is a security vulnerability that arises when an app inadequately validates user input within text fields. This vulnerability allows attackers to inject malicious code, typically scripts, into those text boxes. Let’s break down the attack and its implications:
The Attack Scenario:
- App Vulnerability: The app has a text field where users can enter data. This field lacks proper validation, meaning it doesn’t restrict what kind of information users can input.
- Malicious Script: An attacker creates a script containing harmful code. This script could be designed to steal data from the phone, redirect the user to a phishing site, or disrupt the app’s functionality.
- User Interaction: The attacker tricks the user into entering the malicious script into the app’s text field. This could be done through various social engineering tactics, like phishing emails or messages that appear to come from a legitimate source.
- Script Execution: Once submitted, the app processes the user’s input, unaware it contains malicious code. The script gets executed within the app’s environment, potentially causing harm.
Impact:
The consequences of a text box injection attack can vary depending on the attacker’s goals and the capabilities of the injected script. Potential outcomes include data theft, where sensitive information like contacts, messages, photos, or login credentials can be stolen. Additionally, phishing attacks may occur, redirecting users to fake websites resembling legitimate ones, enabling attackers to steal login information. Furthermore, app disruption is possible, with the script manipulating functionality, leading to crashes, erratic behavior, or rendering the app unusable.
The WebView Connection:
The specific image you described mentions WebView, a component used in mobile apps to display web content within the app itself. Attackers might target WebView through text box injection to achieve similar malicious goals as mentioned above. For instance, a script could be designed to
Redirect the WebView to a phishing site: This would appear seamless to the user since WebViews typically lack an address bar.
Inject malicious code into the WebView’s content: This could steal data displayed within the WebView or manipulate its behavior.
ATTACK SENARIO
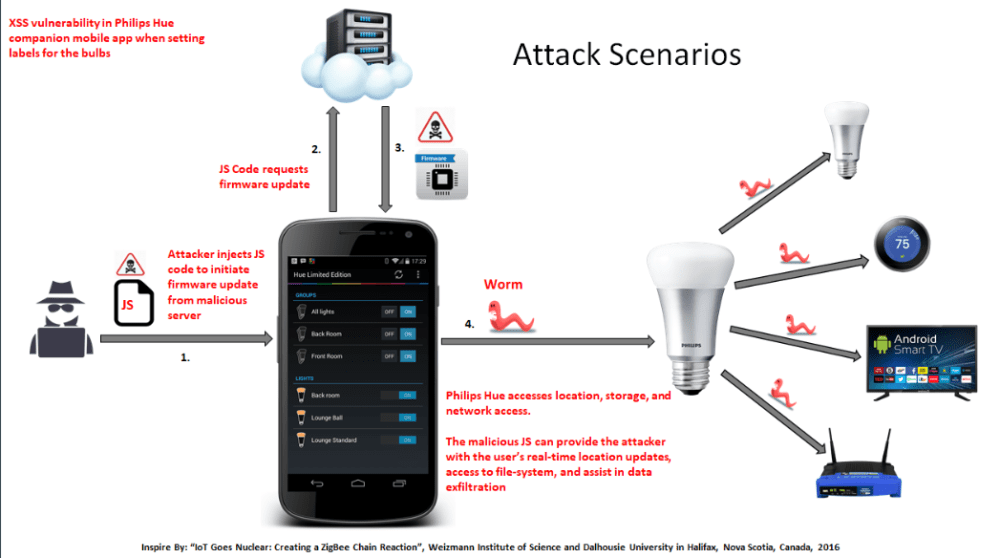
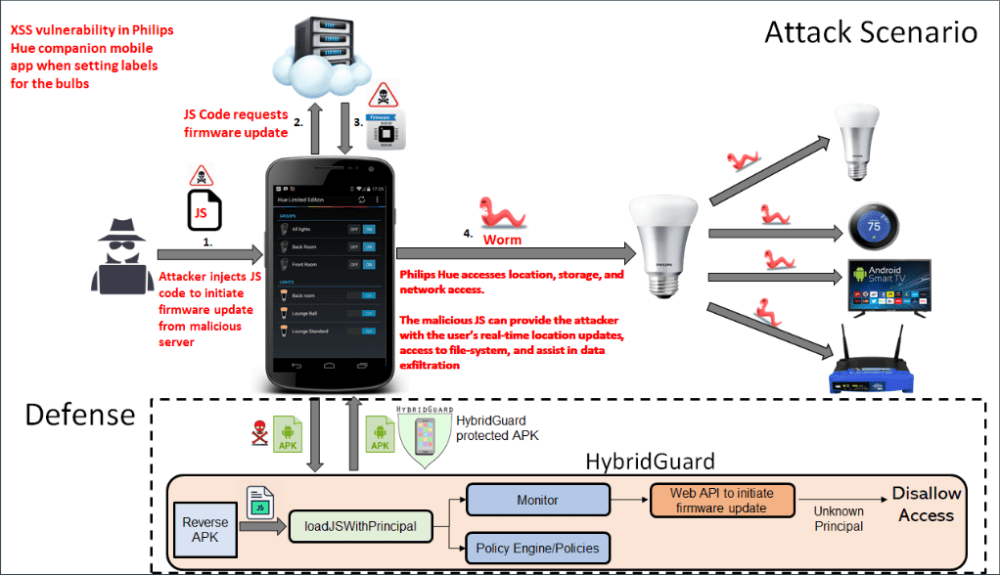
Understanding and Preventing XSS Vulnerabilities
How Does the Attack Work?
Imagine this scenario: An attacker discovers a flaw in the mobile app that allows them to inject malicious code when you set a label for a bulb. When you unknowingly enter a label containing this code, the app processes it alongside the label name. This code might then instruct the bulb to download a firmware update from a server controlled by the attacker.
What are the Risks?
While the exact impact of this specific vulnerability is limited (potentially modifying a small portion of the bulb’s firmware), it highlights the importance of cybersecurity for smart home devices. In broader terms, XSS vulnerabilities could allow attackers to:
- Compromise Your Bulbs: Malicious firmware could grant attackers unauthorized control over your lights, disrupting functionality or even spreading malware to other devices.
- Steal Your Data: Attackers might exploit the vulnerability to steal data from your Philips Hue system, including login credentials or network information.
Challenges
- The IoT companion apps are built using different frameworks and not just Cordova.
- Considering attacks such as XSS, SQLi, Command Injection and Code Injection instead of just malicious third-party JavaScript.
- Communication between the app and IoT device and new attacks requires designing of new policies.